IT is central to business initiatives such as reengineering, knowledge management, the creation of electronic channels of distribution, and the development of digital business strategies. Why are companies outsourcing the activities of their IS departments at such an unprecedented rate when IT has never been more critical to business success?
The motivations for outsourcing are evolving from a primary focus on cost reduction to an emerging emphasis on improving business performance. The traditional rationale of vendor economies of scale and specialization is becoming less convincing. Companies such as Dupont, British Petroleum Exploration, Lufthansa, Swiss Bank Corporation, and J.P. Morgan, with well-run, innovative IS departments that are large enough to accrue the same scale and specialization benefits as a vendor, are nevertheless engaged in significant outsourcing deals. Furthermore, as the growing role and importance of information and communications technologies become widely recognized, companies frequently confront a wide disparity between the capabilities and skills necessary to realize the potential of these technologies and the reality of their own in-house technology capabilities and skills. IT outsourcing is playing an increasingly prominent role in strategies designed to close this gap.
While many companies still follow the traditional out-sourcing model, several innovators are developing new models. Some firms outsource for strategic, not tactical, reasons, to exploit more fully the business benefits of IT. They are pursuing entirely new roles for IT outsourcing and pioneering new paths for IT outsourcing relationships. Consider these examples:
When Xerox Corporation recognized the pressing need to extend IT’s contribution to critical business processes, outsourcing was a key component of its strategy. Dow Chemical realized it was losing IS staff with critical business skills, so it created a unique outsourcing joint venture to enhance career opportunities and gain access to a broader talent pool. Recognizing the benefits of providing its applications systems developers with an entrepreneurial culture and continually updated skills, Philips Electronics decided to restructure its IS organization and out-source systems delivery to a joint venture with a software and systems integration company. As a result, it has itself become a major provider of IT outsourcing services to other companies. To make its IS operations more cost effective and leverage its back-office processing expertise in issuing policies and processing claims, CNA Insurance established a new life-insurance business processing service with its out-sourcing partner as a part of a huge long-term data-center outsourcing deal. In another unusual deal, Swiss Bank Corporation acquired a stake in its vendor, with the intention of offering outsourcing services to other financial services companies.
These examples are 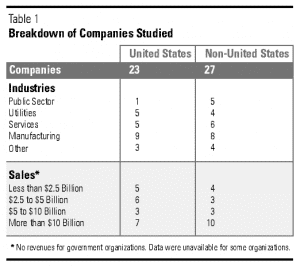 drawn from a study conducted by CSC’s Foundation research program, which interviewed senior executives in fifty companies worldwide that have outsourced some or all of their IT operations .
drawn from a study conducted by CSC’s Foundation research program, which interviewed senior executives in fifty companies worldwide that have outsourced some or all of their IT operations .
The study examined some of the most critical questions about IT outsourcing: How can IT outsourcing help a company achieve its strategic goals? What kinds of outsourcing relationships should it enter into? How can the incentives of client and vendor firms best be aligned through the sharing of risks and rewards? What must senior managers do to ensure the success of these arrangements?
Outsourcing and Strategic Intent
We discovered in our research that while the academic literature and business press discuss IT outsourcing as if it were always driven by a singular focus on reducing the costs and enhancing the efficiency of IT resources, this is in fact only one of three kinds of strategic intent for IT outsourcing .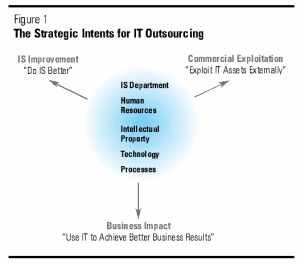 We call this well-established intent “IS improvement.” The other two have more recently emerged as significant factors in many companies’ decision to outsource. Outsourcing for business impact focuses on improving IT’s contribution to company performance within its existing lines of business. The third category of intent, commercial exploitation, focuses on leveraging technology-related assets — applications, operations, infrastructure, and know-how — in the marketplace through the development and marketing of new technology-based products and services. These categories of strategic intent are cumulative, not mutually exclusive: outsourcing agreements focusing on business impact generally encompass a focus on IS improvement as well, and agreements targeted at commercial exploitation usually incorporate elements of the other two.
We call this well-established intent “IS improvement.” The other two have more recently emerged as significant factors in many companies’ decision to outsource. Outsourcing for business impact focuses on improving IT’s contribution to company performance within its existing lines of business. The third category of intent, commercial exploitation, focuses on leveraging technology-related assets — applications, operations, infrastructure, and know-how — in the marketplace through the development and marketing of new technology-based products and services. These categories of strategic intent are cumulative, not mutually exclusive: outsourcing agreements focusing on business impact generally encompass a focus on IS improvement as well, and agreements targeted at commercial exploitation usually incorporate elements of the other two.
The most important message from our research is that the relationship with the vendor — for example, contract type, decision rights, performance measures, and risk-and-reward allocation schemes — must be aligned with the strategic intent underlying the out-sourcing initiative. The literature often attributes failure to achieve the promised benefits of IT outsourcing to its intrinsic weaknesses.4 Our research suggests that these poor outcomes are often due to failure to define clearly the intent and specific goals for out-sourcing, to align the contract and relationship with strategic objectives, to make contracts flexible enough to adjust to changes in the business or technology, and to ensure that the vendor has the capabilities required to meet the objectives for outsourcing.
For example, incorporating performance measures or compensation schemes appropriate to IS improvement in situations where the other kinds of strategic intent prevail may be counterproductive. It is unlikely that contractual metrics that focus a vendor on cost minimization will lead to the development of innovative new systems and applications. Implementing these new systems demands management mechanisms that encourage and reward the vendor for undertaking the risks inherent to innovation. Where ambitions for outsourcing encompass multiple objectives, the contracts and management mechanisms must be even more sophisticated to address the additional complexity.
Moreover, as strategic intent often evolves over time, both formal and informal aspects of outsourcing relationships must change dynamically to stay aligned with the changing intent. One IT executive we interviewed pointed out just how dramatically the goals of outsourcing can change: “Initially our objectives for outsourcing were to do better those things that we were already doing, as well as to bring in new skills, tools, and competencies. As our business changed, our objectives for outsourcing expanded to delivering bottom-line business benefits from IT in a way that was not done before.”
Three Strategic Intents
The three strategic intents for IT outsourcing provide a framework for assessing outsourcing. In discussing each, we focus on the elements of the outsourcing relationship that organization scientists have identified as critical to the success of contractual relationships: the contract type, the performance measurement and evaluation scheme, the compensation system, and the assignment of decision-making rights to the vendor.5 Senior managers must understand that for each kind of strategic intent, the nature of both the risks and rewards are different, and therefore the control mechanisms must be different. The challenge is to design the contract and relationship so that the selected options contribute to the client company’s objectives: IS cost reduction and service improvement, improved business performance, or the creation of commercial ventures.
The company procuring IT outsourcing services must understand the economics of the production process for information services: the cost structure for the delivery of information services, and how this structure is affected by the risks to each party. The company must know how the vendor intends to achieve the desired objectives and be sure to provide appropriate incentives such as asset transfer and performance-related payments.
IS Improvement
Companies that want better performance from their core IS resources — the hardware, software, networks, people, and processes involved in managing and operating the technology and supporting users —have the strategic intent of IS improvement. Their objectives typically include cost reduction, service quality improvement, and acquisition of new technical skills and management competencies. They believe that outside specialists who are better able to keep pace with new technologies and skills, and who use superior processes and management methods, should manage some, if not all, of their IT services.
Our research identified four levels of ambition for IS improvement 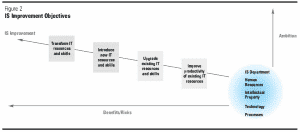 . The first two (improve productivity of resources and upgrade technology and skills) are well-established aims of IT outsourcing contracts. The structure of the deals, however, has changed considerably as technology requirements have changed and as companies have learned from experience. Two noteworthy examples are Kodak and British Petroleum Exploration (BPX). While both companies selectively outsourced functions of their IS departments to three different vendors and structured separate contracts with each one that focused on tailored IS cost and productivity improvements, the underlying philosophies and management structures in the two cases were very different.
. The first two (improve productivity of resources and upgrade technology and skills) are well-established aims of IT outsourcing contracts. The structure of the deals, however, has changed considerably as technology requirements have changed and as companies have learned from experience. Two noteworthy examples are Kodak and British Petroleum Exploration (BPX). While both companies selectively outsourced functions of their IS departments to three different vendors and structured separate contracts with each one that focused on tailored IS cost and productivity improvements, the underlying philosophies and management structures in the two cases were very different.
Kodak pioneered the now-prevalent model of managing outsourcing relationships as strategic alliances.6 Its collaborative approach facilitated joint problem solving and process improvement activities, enabled the retained IS group to control the interface to business units served by the outsourcing vendors, and made it easier to assimilate the vendors into Kodak’s retained IS processes. The outsourcing agreements were structured to allow the suppliers to make a fair profit, and to encourage them to invest in improving the assets they took over. Separate long-term cooperative relationships covered management of its data centers, desktops, and networks, and Kodak explicitly chose to act as its own prime contractor. Contracts contained neither formal incentives nor penalty clauses, but the understanding that, if suppliers performed well, Kodak would make more use of their resources (thus increasing their revenue and profit) was implicit in the relationships. Stipulations such as annual renegotiation of service levels and the requested volume of services kept the multiyear contracts flexible. The contracts emphasized service delivery, process metrics to maintain consistent performance, and early identification and resolution of problems.
BPX had a more unorthodox approach. Like Kodak, it outsourced to three vendors but appointed the strongest in each of its three major regions as prime contractor. The model of selective outsourcing to multiple vendors with one acting as the prime contractor has since been adopted by other companies such as Dupont and J.P. Morgan.
In contrast to Kodak’s collaborative partnerships, BPX’s integrated outsourcing relationships take advantage of its market power and of the increasing maturity and competition in many segments of the IT outsourcing market. This “best of breed” approach matches the skills of each vendor to BPX’s needs, while the structure of the contracts minimizes the effort required to manage multiple vendors. BPX frequently measures to verify continually that the services it receives match best practice in quality and cost. Each vendor is expected to subcontract services that can be performed better by others. Contracts are shorter than usual for IT outsourcing — two years for networks and five years for data center and applications. In theory, this approach gives BPX flexibility and makes the company less vulnerable to escalating fees and outdated technology than if it were tied to a single vendor. But there are some downsides. BPX must sometimes coordinate and resolve problems when issues cut across geographic boundaries or the vendors’ competing incentives. Replacing vendors becomes difficult because a new vendor would have to coordinate its service not just with BPX but with the other providers as well. Lastly, with a shorter horizon, vendors are less willing to invest to improve IS performance since there may be insufficient time to recoup costs.
As the market for IT outsourcing matures and changes in technology continue, companies are more ambitiously pursuing IS improvement. Organizations such as Guinness, Owens Corning, and Canada Post have sought to introduce entirely new capabilities and skills. Guinness, for example, planned to transform its IS management by standardizing processes, core business systems, and technology platforms globally. Guinness executives recognized that the company did not have the skills and resources necessary to achieve such a transformation; outsourcing was a potential solution. Each business unit negotiated its own agreement with a preferred vendor within a master framework.
This approach is different again from those of Kodak and BPX. The primary motivation was the desire to implement consistent standards, technologies, processes, and management systems across the company worldwide. Thus Guinness found it desirable to work with a single vendor with the skills, scope, and leverage to implement global policies. Although there is some risk in relying on a single vendor for an ambitious change agenda, the preferred supplier approach can be a sound choice in a decentralized company with global operations. Guinness managers believe that the company will benefit from outsourcing not just by achieving economies of scale across the total business, but by remaining current with new technologies and directing key resources to major projects. Moreover, the benefit of its evolutionary approach to outsourcing is that each implementation can build on the lessons learned from previous ones.
Lessons for Managers Pursuing IS Improvement.
These and other case examples from our research demonstrate the wide variety of approaches to out-sourcing for IS improvement. Success comes through exploiting economies of scale and expertise, deploying proven processes for cost reduction and service improvement, and bringing distinctive technical expertise to bear for the client. Causes of failure include the vendor’s lack of appropriate technical and management skills, cost shifts and postponements instead of real reductions, and added coordination costs that exceed the savings from outsourcing. Thus, achieving the goals hinges on technical and operational processes and skills. Accordingly, management control mechanisms (contract type, performance measures, reward and penalty schemes, and decision structures) should focus on IS services (see Table 2), for example, network provision, data-center operations, applications program maintenance, and new systems development. Appropriate performance metrics include network response time, problem-resolution cycle time, cost per user, and function points.
A critical aspect of contracts for IS improvement is the pricing of technology services. Vendor compensation is typically based on a pricing schedule for a set of technology services, either specified in advance for the duration of the contract or negotiated each year. Predetermining a price schedule that will reflect future costs is difficult, given the uncertainty in future technologies (and their associated costs) and in business conditions. When specifying a price schedule in advance, it is critical to create a highly competitive vendor selection process to ensure that the proposed prices are competitive. Companies must also incorporate frequent benchmarks to ensure the use of best practices and provide for renegotiation of prices if business and technology conditions change substantially.
The nature of the relationship — contractual or partnership-based — should depend on the risks and uncertainty associated with delivering the outsourced services. When requirements are well defined and outcomes are observable, the relationship should have a greater focus on contractual elements. BPX exemplifies this point. On the other hand, when there is more uncertainty about requirements, a partnership approach may be more desirable, although this approach requires contractual specificity where appropriate. Kodak recognized this necessity in its outsourcing agreement. More recently, Swiss Bank and Guinness forged flexible partnerships with out-sourcing service providers in order to accomplish similar objectives.
Will these ambitious outsourcing relationships prove successful? In our view, the requirement for success is to strike the right balance between risk and reward for the vendor and client, and ensure that the client is significantly involved in the improvement initiatives, perhaps even contributing complementary competencies. We also believe that transferring ownership and responsibility for IT assets — particularly people and technology — from the customer to the out-sourcing vendor is critical to success. Ownership gives the vendor the incentive to continue investing in those assets.
Business Impact
Many IS organizations are struggling to develop the right mix of technical and business skills to exploit technology. As a result, many companies are looking to the IT outsourcing market for help, on the premise that outsourcing vendors’ state-of-the-art skills, capabilities, and proficiency at recruiting and managing technologists make them better than internal IS organizations at using IT to improve business results.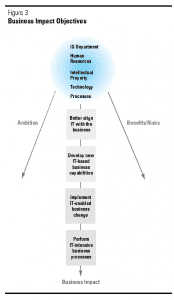
We define this strategic intent for IT as business impact. Its primary goal is deploying IT to significantly improve critical aspects of business performance. Realizing this goal requires an understanding of the business and the link between IT and business processes, and the ability to implement new systems and business change simultaneously. This form of outsourcing brings new skills and capabilities that link IT to business results rather than those related purely to technology. In several instances of out-sourcing for business impact, we found that the most effective approach focused on jointly developing complementary skills and capabilities, rather than simply relying on those of the vendor.
Our research showed four levels of ambition for business impact. They range from the modest goal of better alignment of IT resources with business needs to the delivery of new IT-based business capabilities and competencies. These goals might include the capabilities to deliver innovative information systems (for example, automating order fulfillment, inventory management, or customer management processes) and the competencies related to business process analysis and management (for example, using technology to reengineer business processes). We view process outsourcing, in which the vendor is charged with performing the business process and achieving targeted business results in addition to technology and systems management responsibilities, as a special case of outsourcing for business impact.
Many organizations must simultaneously create a new IT capability — the new systems, reengineered work practices, reskilled staff, and entrepreneurial culture — to compete in the emerging digital world while maintaining (and improving) the status quo. Our research strongly suggests that this is very difficult for IS groups to do on their own. Most lack the necessary technical talent, management skills, and financial resources. Outsourcing can free up financial resources and management attention, support the operation and maintenance of existing systems until they can be replaced, provide career paths for staff with legacy skills, and supply technical and business know-how to augment new initiatives.
A good example is Xerox Corporation. Despite being financially healthy and technologically advanced, the $18 billion document products, systems, and solutions giant decided to outsource as part of its move to completely transform the IT resource — technology, processes, and people. Outsourcing was integral to the company’s broader effort to reengineer and retool its business capabilities. The company out-sourced most of the existing infrastructure and 70 percent of its IS staff people to EDS — thereby giving them an opportunity to develop new career paths. This freed financial and management resources to concentrate on creating future business-critical IT infrastructure and applications and acquiring new IT-related skills for remaining staff.
In the words of Pat Wallington, CIO, “We want to focus our internal staff on moving us to the environment that will support us tomorrow.” According to Jagdish Dalal, a Xerox executive then involved in the outsourcing and reengineering initiatives, “I would not have even thought of reengineering if we hadn’t outsourced, because we would have been busy reorganizing, letting people go, consolidating data centers, whatever. Xerox had to reduce its IT spending and redirect it, and the best way to do that was out-sourcing.”
Xerox designed the outsourcing contract to ensure continuing high-quality and cost-effective service levels from the existing IS processes and resources while making it possible to eventually replace them by funding new IT infrastructure and systems. The contract addressed the company’s cost and service objectives, but more importantly, it made liquid a significant portion of the IT asset base to provide seed money for the new IT infrastructure and for process and systems reengineering. Additional funding is anticipated from the savings generated as legacy systems running on outsourced mainframes are replaced by new systems running on client-server infrastructure. Xerox’s main challenge is to build new systems fast enough to retire the outsourced legacy applications in time to release funds for further new systems development.
Increasingly, companies are looking to their outsourcing partners for new or improved IT-based business capabilities that can have a direct impact on business performance — such as yield management, dynamic forecasting, efficient response systems, logistics optimization, or customized marketing and product offerings. But is IT outsourcing a viable strategy for developing and exploiting these important business capabilities?
A midsized chain of health and beauty stores in Europe that we shall refer to as HealthCo outsourced its entire IS department to transform its contribution to business goals. Like Xerox, it set an ambitious agenda to change IT and the business and to prime its competitive capacity. Major alterations in strategy necessitated the transformation of the business model, in particular, reengineering the supply chain to optimize cost and speed of end-to-end operations. Unlike Xerox, HealthCo was not in a position to create the new systems and infrastructure needed to support its plans for business expansion. Instead, it relied heavily on its IT outsourcing partner’s resources, capabilities, and skills to change its operating model and to deliver powerful new IT-based business capabilities. Ultimately, HealthCo intends to further develop its core competencies — product sourcing and merchandising — and to develop a core network of world-class partners to do everything else. This goal will require new systems that are tightly integrated with the systems of its strategic partners.
HealthCo believes that outsourcing relationships can yield significant business benefits and that exposure to risk can be controlled through a close and mutually beneficial relationship underpinned by performance-based contracts. The vendor’s financial reward is tied not only to IS performance but also to HealthCo’s business success, particularly on selected systems where benefits are clear and directly related metrics are available. An example is assortment planning, a critical process for most retail stores, which involves estimating quantities and varieties of product lines. Its outsourcing vendor is developing the new system at cost and will be paid a percentage of the bottom-line improvements it creates.
The telecommunications services provider, Pacific Bell Telephone, also required substantially improved IT-based business capabilities to speed up new product introductions and service enhancements. The main impediment was its aged and inflexible customer-billing system (which is the heart of all operations and feeds into all its other information systems), but the IS group lacked the skills and competencies necessary to replace the old system and manage the new one. The group engaged an IT specialist organization to do the work; this relationship soon evolved into a joint venture (called the Solutions Engineering Center of Excellence) to facilitate knowledge transfer and continued development of the system after its implementation.
As one executive put it: “We figured that, by working together in an arrangement other than buyer and seller, we could build capabilities on an accelerated basis. I also wanted an effective technology transfer between their experts and our own internal people.” The joint venture consisted of 800 development specialists, 70 percent from Pacific Bell and 30 percent from its outsourcing partner. It spread the risks and costs of the ambitious new systems project between the partners: the outsourcing vendor is paid a bonus above a flat fee if the joint venture and the systems implementation meet specific efficiency, service, and quality goals.
Dow Chemical used an equally innovative approach to outsourcing to create new IT capabilities. It had difficulty retaining skilled people to manage increasingly bigger and more complex IT-enabled business change projects and to implement systems integral to business performance. The applications development manager at Dow saw that outsourcing offered a way both to build competence in those areas where he wanted his group to excel and to off-load responsibility for everything else to an experienced partner. Dow hoped to tap into the partner’s expertise in applying IT to the business and developing critical in-house IT capabilities (business impact) and to benefit from better IS resource management and reduction of fixed costs (IS improvement).
Under an outsourcing arrangement with Andersen Consulting, Dow set up three development and support centers of expertise, two in the United States and one in Europe, employing a mix of Dow and Andersen staff and contractors. Within the centers, people work on teams jointly led by Andersen and Dow managers. Team responsibilities are also split. Typically, Dow takes sole responsibility for managing the relationship with the business, architecture, and running IS applications in the business units, areas in which it had proven competency. Andersen is responsible for development and testing. Both share the responsibility for systems implementation and productivity.
Some companies that outsource IT for business impact ask their outsourcing partner not only to implement new systems with bottom-line impact, but to take on further responsibility for implementing changes in the business as well. Rolls Royce Aerospace Group’s deal with EDS combines consulting with systems integration and outsourcing to cover a range of business transformation initiatives including time to market, customer service, supply chain management, and manufacturing and engineering operations. Farmland Industries, Inc. and Ernst & Young LLP have established a joint venture called OneSystem Group LLC. OneSystem Group will serve as a technology vendor and contractor for the continuous improvement of Farmland’s operational activities, such as its international supply chain, finance functions, and integrated human resource services. CoreStates Bank and Andersen Consulting have formed an outsourcing alliance to enhance CoreStates’ revenues by facilitating new product development, to improve the speed and efficiency of bringing new products to market and increase customer service quality, and to use Andersen Consulting’s expertise to give CoreStates access to new capabilities and technologies.
A few companies have gone even further and commissioned their outsourcing partner not only to deliver IT to improve business processes, but to operate and manage those processes as well. This growing area of business process outsourcing is being penetrated increasingly by IT outsourcing vendors expanding their capabilities in areas such as insurance claims processing, logistics, payroll, municipal administration, airline operations, airport management, power distribution management, and so on. It is an attractive market for IT outsourcing vendors because the profit margins are significantly higher compared to the relatively commoditized markets for pure IT services.
Lessons for Managers Pursuing Business Impact.
Our research identifies business impact as a significant and growing objective for IT outsourcing, and one that is driving a fundamental change in the nature of the relationship between the user and the provider of IT outsourcing services. Further study of this emerging market is needed, but our research suggests that the agreement must emphasize shared risks and rewards tied to tangible business results. A conventional outsourcing contract for simple commodity transactions and services is insufficient. Different types of risk and reward contracts apply in different circumstances. For example, companies wanting cost-effective IT-enabled business solutions that require an understanding of their business should enter into arrangements that give the vendor incentives to learn about the customer’s business while still maintaining competitive pressures on the vendor. A preferred supplier arrangement is one such approach. If specialized expertise and knowledge of the business are essential and tight control over the resources involved in the work is crucial, then a strategic alliance or joint venture may be required.
Success factors are more business oriented than technical — for example, understanding the operation, fitting IT to business needs, being able to manage change projects, and having the right balance of management expertise and technical know-how. Pricing provisions should tie vendor compensation to value received by the client. Payments and incentives should be determined by measures of business process performance (such as the cost, quality, and productivity of processes) as well as by measures of results (like contribution to top-line revenue growth, bottom-line profit increases, or shareholder value gains). The contract should also set out how key people are deployed, how confidential information and proprietary resources are treated, and whether to confer preferred supplier status on the vendor (see Table 1).
Companies that engage in outsourcing for business impact recognize the significant potential of technology in creating business value. In these situations, it is crucial for the internal IS organization to retain ownership of the user management and IT innovation processes focusing on the discovery of new ways to exploit technology in the business. Given the strategic importance of these activities, it may be necessary to make the continuous transfer of knowledge about the impact of emerging technologies explicit in the outsourcing contract.
Commercial Exploitation
Outsourcing information technology with the strategic intent of commercial exploitation aims to improve the return on IT investment by generating new revenue and profit or by offsetting costs. The means by which IT assets can be leveraged commercially range from licensing systems and technologies developed initially for internal use, through selling IS products and services to other firms, to launching new IT-based businesses.
Our study discovered that companies pursuing commercial exploitation were often those with innovative information systems. Many come from technology-intensive industries, such as air transport and financial services, and have mission-critical systems that are expensive to maintain and enhance. They find additional expenditure on migration to new technology platforms or to exploit technological advances like the Internet difficult to fund based on internal returns alone. Only when the broader revenue potential of the proposed innovations is taken into account does the investment become viable.
Many companies also find it increasingly difficult to acquire, develop, and retain the people and technical know-how necessary to maintain existing complex systems and implement new ones. Furthermore, few IS organizations have the capabilities required to exploit IT in the marketplace: the know-how to commercialize and sell IT products and services originally developed for use by a single company, the ability to establish new distribution channels for IT-based products and services, the skill to port systems to various technology platforms, and the wherewithal to support and enhance products and services after they are sold. One way to gain those capabilities is through relationships with outsourcing vendors.
We expect to see an increase in outsourcing deals with the intent of commercial exploitation. As IT becomes more tightly integrated with business processes, as it grows in importance as a component of products and services, and as distribution and communication channels become electronic, the market for industry-specific applications of IT and for systems that support business processes becomes extremely large.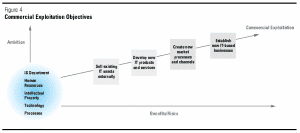 Moreover, the emergence in many industries of standard platforms and shared services makes it easier to resell information systems applications developed in one company to others in the industry. Sharing the costs and risks of commercialization with outsourcing partners can help maximize return on IT investments. For their part, the outsourcing vendors look to client firms as unique sources of the industry-specific expertise, know-how, and technology assets that are essential to developing new and innovative systems in complex and competitive industries.
Moreover, the emergence in many industries of standard platforms and shared services makes it easier to resell information systems applications developed in one company to others in the industry. Sharing the costs and risks of commercialization with outsourcing partners can help maximize return on IT investments. For their part, the outsourcing vendors look to client firms as unique sources of the industry-specific expertise, know-how, and technology assets that are essential to developing new and innovative systems in complex and competitive industries.
While only a few companies are now pursuing commercial benefits from outsourcing, their experiences yield many valuable lessons about how to grow existing businesses and develop new ones. Our research identified four levels of ambition for commercial exploitation. The most common aims are to gain revenue by selling existing IT assets (applications systems, access to infrastructure, technical expertise) to other companies and to develop and commercially exploit new IT products and services. More ambitious objectives involve attempts to restructure industries by building new electronic market processes or distribution channels (such as Web-based travel reservation systems and on-line trading) and creating entirely new IT businesses (typically, applications software, IT consulting, and business process outsourcing).
All companies considering IT outsourcing — whether their strategic intent is commercial exploitation or not — should be aware that the vendor with which they contract may seek ways to commercially leverage the assets (people, systems, and technology) it acquires by using them to service other accounts or by selling or providing other firms access to them. Companies should therefore realistically assess the potential commercial value of outsourced IT assets and understand how the vendor intends to use them. This should be factored into the contractual terms of the relationship — for example, by increasing the amount paid by the outsourcing vendor for the assets it receives in the deal, by discounting the price for services, or by setting up a revenue-sharing arrangement.
When Dupont sent out a request for proposal (RFP) for outsourcing services, it prepared two documents. One was a typical RFP for service; the other was a special request for business relationship that was both a prospectus describing the commercial potential of Dupont’s IT assets and an invitation to vendors to propose innovative ways of exploiting these resources in the external IT market and of sharing the rewards. When the UK’s Inland Revenue awarded its outsourcing contract, it included an “open book” agreement by which the revenue department gets a share of any profits the computer services company makes by selling spare capacity on the department’s systems.
Other major companies setting up commercial ventures in developing and marketing new IT-based products and services jointly with outsourcing partners include Hyatt Hotels, Lufthansa, Ryder Systems, and Ameritech. Swiss Bank Corporation (SBC), one of the world’s leading retail, commercial, and investment banks, is a striking example. SBC went into IT out-sourcing with Perot Systems to speed its IT infrastructure transformation and to explicitly leverage in the marketplace its already-substantial investment in IT expertise and infrastructure. The two parties signed a twenty-five-year contract worth an estimated US $208 million per year; 700 IT specialists were transferred to a new division created by the vendor to provide state-of-the-art systems and network services to SBC and to other customers in the global financial services industry.11 SBC received a nonvoting equity stake of 24.9 percent in Perot Systems.
Expectations for these types of commercial ventures are high, and meeting them can be tricky. Delta Air Lines urgently needed access to new, state-of-the-art technology and skills to speed the migration of its core information systems from a mainframe environment to distributed, open client-server platforms. Like SBC, Delta also viewed its IT outsourcing arrangement as a way to create new avenues for revenue generation by selling technology products and services to other companies in the travel and transportation industries.
Delta did not sign a contract with AT&T, but instead created a joint-venture company, TransQuest Information Solutions, owned equally by the two organizations. Delta’s outsourcing contract was with the jointly owned company. Thus Delta retained some ownership and control of IS, while putting it into the commercial context, and gained the benefit of new capabilities and expertise. About a year after its start, the joint venture encountered serious difficulties. The executive who headed the AT&T IS unit, a key player in the relationship, unexpectedly left the company. Not long after, AT&T announced that it was breaking up into three separate companies — a communications services company (AT&T), a communications equipment company (Lucent Technologies), and a computer products and services company (NCR). Responsibility for the TransQuest venture was given to NCR but the industry, technical, and commercial expertise important to Delta was scattered across all the newly divested AT&T units. The partnership was eventually dissolved, and Delta now has full ownership of TransQuest. It has abandoned its commercial ambitions to concentrate fully on finding ways to acquire, develop, and fund crucial new technology capabilities.
A recent development is the use of IT outsourcing to create new electronic market processes and distribution channels. The transportation, hospitality, and insurance industries rely heavily on information and computing, often using outdated computer architectures, in a changing marketplace with unclear direction. A leading travel agency, BTI Americas, for example, entered a strategic alliance with its out-sourcing vendor to build new electronic channels and services to move from transaction-oriented service to travel-management service. Gothaer Corporation, one of Germany’s biggest insurance groups, formed a new joint venture with IBM Germany to handle all Gothaer’s data processing, internal and external networks, and the development of applications software. The two companies, along with other partners, have also formed a software development company called Allegemeine Versicherungssoftware GmbH (General Insurance Software) in which Gothaer holds the majority stake. The new company’s mission is to create and market applications software based on standard architectures, such as IBM’s Insurance Application Architecture, to other insurance companies.
The most ambitious aim of IT outsourcing for commercial exploitation is to create a new, stand-alone IT business. Public Service Company of Colorado (PSC) and IBM forged a partnership that combines IT out-sourcing and energy-management application development. Under the agreement, Integrated Systems Solutions Corporation (ISSC) took responsibility for managing most of the utility’s IT infrastructure, including its data center, workstations, computer help desk, and intrastate microwave network. At the same time, ISSC and a new PSC subsidiary, E Prime, will develop IT-based applications to support its new customer-service energy management business. CNA Insurance created a new business with its outsourcing vendor CSC to perform claims processing and policy issuance for other insurance companies and financial services firms that are just entering the life insurance market. The venture combines CSC’s IT management expertise and object-oriented applications software with CNA Insurance’s business process know-how.
A particularly successful example of commercial exploitation is N.V. Philips, the Dutch electronics giant, which evolved its outsourcing intent and relationship over several years to create a new line of business. Philips outsourced its applications development function but not IT infrastructure and support, an unusual approach. Rather than sign a standard outsourcing contract, it set up a joint venture, BSO-Origin, with the Dutch software company, BSO Beheer, and transferred many employees from around the world into the new company. The deal gave Philips an initial 15 percent equity share of BSO-Origin and two seats on the management board. The communications services and data center people moved to a new wholly owned subsidiary called Communications and Processing Services (Philips C&PS) that was set up as a profit-and-loss center and encouraged to sell its IS services externally.
Philips believes that its approach to IT outsourcing has paid off, though implementation took longer than it had originally anticipated. Initially, there was a significant cultural mismatch between BSO and ex-Philips staff. BSO was a small, entrepreneurial software company operating in Europe, mainly in the Netherlands, while Philips was a huge, hierarchical multinational. Many Philips employees enjoyed working in an international company and culture and did not want to work for a company like BSO-Origin. Not surprisingly, some of the transferred staff subsequently resigned. Recently, Philips C&PS and BSO-Origin have cooperated to deliver services jointly to external customers. Philips positioned itself to expand its outsourcing and insourcing arrangements commercially through the experience it gained with BSO-Origin. The jointly owned company has acquired other software service providers, and in early 1996, BSO-Origin and Philips C&PS merged to create an expanded commercial IT entity of more than 10,000 people with a combined revenue of US $1.5 billion.
Lessons for Managers Pursuing Commercial Exploitation.
Because of the risks and rewards associated with commercial exploitation of IT, the issues of sharing and control are unique. For these deals to succeed, they must contain adequate incentives for each party to share costs and risks over the course of the relationship. Given the uncertainty in the level of required investments and the underlying risk and potential payoffs, it is difficult, if not impossible, to write a contract that specifies each party’s commitments for the future. Accordingly, relationships should be built around strategic alliances, joint ventures, and joint ownership arrangements that align incentives at the level of business outcomes. In managing the relationship with the outsourcing vendor, companies should focus performance metrics on results such as increased return on assets, ratio of IT spending to recovered costs, new revenues, net profits, gains in market share, launch rate of new products and services, and development of new businesses and market channels.
When commercial exploitation is the underlying strategic intent for outsourcing, factors related to product development, technical innovation, and sales and marketing become key determinants of success. The chief impediments to success include misjudging or failing to realize synergies of assets and capabilities, failing to fulfill commitments to internal customers, and perhaps most critical, ensuring that the rewards received by the partners are commensurate with the risks that each assumes. These ventures simply do not work unless each party makes a significant investment of management and staff, technology resources, and funding.
An important pricing provision relates to the charges for services provided to the primary internal customer and, in particular, whether they should be provided at cost or cost plus profit. Other important provisions include specifying ownership of technology assets, particularly jointly developed ones, protecting intellectual property rights for intangibles such as applications software, control over key staff, and whether and how products and services are sold to competitors.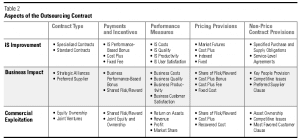
IT commercial exploitation can be a viable way to generate revenue, raise capital, recover costs, recruit and retain scarce talent, and develop and broadly leverage capabilities. Success, however, requires the courage and patience to make a long-term commit- ment, an ability to assume greater risk in return for potentially greater rewards, and, of course, IT assets and capabilities with demonstrable value in the marketplace. For the longer term, it is also important to create mechanisms to identify continuing IT innovations in the business that can be exploited externally.
Conclusion
The findings of our research strongly establish the importance of understanding the different types of strategic intent for IT — IS improvement, business impact, and commercial exploitation — and the role that outsourcing can play in pursuing each. In this article, we have argued that there is no “one size fits all” approach to IT outsourcing — each type of strategic intent for IT outsourcing requires different approaches and tactics to be realized successfully. In evaluating IT outsourcing opportunities and structuring relationships, managers for IS and the business should remember the primary requisites for success — consistency, competency, compatibility, and continuity:
Design the outsourcing contract to consistently reflect and reinforce each strategic intent pursued.
Our most important finding is that the strategic intent for outsourcing must drive the operating philosophy of the relationship and be reflected in the critical features of the outsourcing contract: contract type, pricing provisions, reward and penalty mechanisms, performance measures, and nonpricing provisions. Be consistent in defining what you want from the out-sourcing relationship and make sure your agenda and your outsourcing vendor’s agenda are aligned.
Make sure your organization and the outsourcing vendor have the right mix of competencies and know-how.
It is not sufficient simply to accept vendor claims of capabilities, even if the company is prepared to make a contractual commitment. It is important to test whether the vendor has the competencies it needs to deliver what you expect both now and in the future. For IS improvement, factors such as economies of scale, technical expertise, and IS management processes must be validated. Business impact requires change management competence and reengineering skills as well as process know-how. Commercial exploitation demands sales and marketing prowess, an established customer base, and viable channels of distribution.
Alternatively, the buyer of outsourcing services must ensure that it retains an IS organization with the capabilities required to manage the relationship well. Investments in training and staff recruitment may be necessary to ensure the right people and skills. Key competencies include IT performance measurement, IT services market tracking, project management, and deal making, negotiation, and conflict resolution. Market expertise, finance, and licensing-management skills are also required if the client intends to exploit its systems commercially.
Make sure your organizational culture and work practices are compatible with your partner.
Out-sourcing vendors must be chosen with care, paying particular attention to shared objectives and cultural fit. For a successful outsourcing relationship, the operating styles and cultures of both organizations, client and vendor, must be compatible at all levels. Managing for results requires sustained effort by both the client and the outsourcing vendor. Both parties must develop a mutual understanding of their work processes and identify critical aspects of the relationship.
Enable continuity by designing contracts and relationships to anticipate change.
The intent and ambition for outsourcing may change over the course of the contract as the business conditions and technology evolve. It is important therefore to anticipate shifts in these priorities and to build flexibility into contracts and alliances to deal with them. The contract must be resilient enough to deal with future changes in requirements. Set up the relationship structure and management mechanisms to work successfully with the outsourcing vendor over the long term.
While ambitious business and technical objectives for information technology are always difficult to achieve, we believe that the chances of success are greatly increased when strategic intent is well understood and the relationship is managed to address these critical issues.
0 Comments
Leave A Comment